COVID has accelerated some drastic changes in the modern workplace and the way companies utilize their office spaces. With such a quick transition to reenvisioning the office, we have put together the full evolution of these changes along with the physical security trends that companies are adopting in order to adapt.
Table of contents
- The 4 Post-COVID Changes In The Workplace
- Physical Security Challenges in Post-COVID Offices
- The Future of Physical Security in the Office
Also, read
- Best Face Recognition Access Control Systems
- Managing Satellite Office Security in the New Work Environment
- Top Apartment Amenities: A Guide for Landlords & Renters
The 4 Post-COVID Changes In The Workplace
1. Offering Flexible Work Hours
Remote work has made companies realize that employees not only don’t need to be in the office to be effective, but they also don’t need to work the traditional 9 to 5 workday. Nor do they want to.
So, it’s not a matter of if companies will begin adopting flexible schedules, but when. Some have already gone as far as to offer a completely asynchronized work environment.
An asynchronized work environment is a relatively new concept that refers to a workplace with no fixed hours. Employees choose the hours they work and the location in which they work them.
And according to a recent study, 67% of those ages 16 to 34 would choose to work in an asynchronous environment if given the opportunity. But adopting this way of work doesn’t just have benefits for employees. It’s also the key to efficiency.
2. Permanently Incorporating Hybrid and Remote Work
The discussion about permanent hybrid and remote work is a popular one. And for good reason. Big companies like Twitter have instituted a permanent remote work policy for their employees and others have followed suit. With such a big transition, there must be some merit behind it.
According to the IWG global workspace survey, 85% of participants report increased productivity as a result of greater flexibility afforded by hybrid and remote work models. And 65% of those same participants believe businesses who tailor the work environment to the work function of staff are more productive. But hybrid and remote work are not only good for boosting productivity. They are also beneficial to operations. In fact, 65% of businesses say the flexible workspace helps them reduce CAPEX and OPEX, manage risk, and consolidate their portfolio.
So, it’s no surprise that 58.25% of companies plan to adopt a hybrid work model post-COVID and only 15.5% plan to return to the office full-time. This model is also very important for hiring purposes in the future, as well.
When faced with two similar employment offers, over 80% would turn down the offer that did not offer flexible working.
3. Growth of Flex Workspaces and Coworking Models
Incorporating a hybrid or remote work model also means companies will need to adjust their physical office space strategy, which is where flex and coworking spaces come in.
Flex and coworking spaces are shared environments that can be rented by any company for any number of employees in order to create a collaborative working environment on a temporary basis.
According to CBRE, 86% of surveyed respondents see flexible office space as a key component to their future real estate strategies. This number increased from 73% in June 2020.
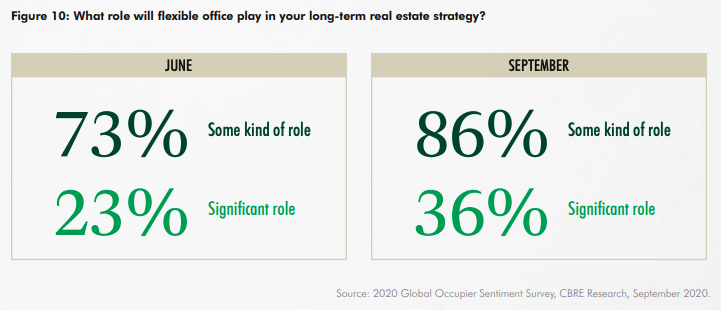
This 13% jump in a matter of 4 months can likely be attributed to the success and productivity of the remote workforce. In fact, almost half of those same respondents attribute the main reason for implementing a coworking model is to provide a network of locations to accommodate a mobile workforce.
4. Increasing Satellite Office Locations
We tend to think of companies in terms of their headquarters. This is the central hub for businesses, however there is a complete network of smaller offices that branch out from the headquarters that many times go unnoticed. These satellite offices, sometimes referred to as branch offices, are extensions of the headquarters in a different location.
Companies are increasing satellite office locations for several reasons:
- Provide a physical, collaborative space that accommodates new remote work policies
- Balance the urban, headquarter office with the remote work lifestyle
- Support an increasingly dispersed workforce as employees relocate due to remote work opportunities
While there has been speculation about the future of offices, they are by no means going away. The result, rather, will likely be this increase in satellite office locations that we are seeing and simply a downsizing of office headquarters.
Physical Security Challenges in Post-COVID Offices
The drastic changes in modern work culture have accelerated faster than anyone could have predicted. The growth of the remote and hybrid work environment had been slowly progressing even before the COVID-19 pandemic. But now, what would have been years in the making, is in full effect within a matter of months. With such a rapid transition, companies have had little to no time to plan for the challenges that these changes bring.
So, what are the physical security challenges that companies are facing and need to pay attention to now that they have rolled out a new remote model for their workforce?
More and more people are coming in and out of offices with less predictability than ever before
Staggered scheduling, hybrid work models, and coworking spaces are causing huge amounts of inconsistency in office foot traffic. Employees are coming and going with less predictability, and this is making credential management more difficult for IT, security, and facility teams. Issuing new credentials, managing dormant credentials, and revoking credentials requires much more time and oversight if people are coming in rarely. And fragmented and time-consuming credential management causes gaps in physical security and greater risk of physical security threats.
IT teams are battling a record volume of cybersecurity threats
What does cybersecurity have to do with physical security? You only need to look as far as the Oldsmar Florida water treatment plant to understand how critical cybersecurity is to physical security. And with the growing number of threats since COVID-19, IT teams have been forced to become reactionary instead of proactive. Simply put, this means that companies need to ensure their physical security protocols are airtight in order to ensure that IT teams can channel their energy into proactive cyber protection.
Disparities in access control systems
An on-site access control system will only store the users that were manually added into the local server. The users are not transferable between locations, even if they are within the same company, because there is no way for the systems to communicate with one another. This makes it extremely hard for companies utilizing several locations to manage the access credentials of their employees. And, it becomes even more complicated now that companies are increasing their number of satellite office locations.
The growing utilization of flex and coworking spaces also needs to be taken into consideration. Different coworking spaces have different access control systems which further adds to the complication because the credentials and system nuances will be different depending on the host.
Finally, our current economic environment is seeing a lot of mergers and acquisitions take place. Acquisition targets rarely have the same access control system as the acquirer and that leads to a hodge-podge of systems as well.
Flexible offices are struggling to find a streamlined way to distribute access
Flex offices and coworking spaces see plenty of turnover. There may be a company that reserves office space for just a few hours, and another company will occupy the space the next day. These flexible work environments are struggling to manually manage visitor pass and access credentials even with a dedicated staff member to manage it. Distribution of credentials takes a lot of coordination, not to mention manually updating the access system to reflect the appropriate credentials and new users for that day.
Inconsistent on-site staff is making package management and receiving deliveries more difficult
As employees and facility staff are working in the building with less predictability and during non-traditional hours, companies are running into problems with package management and receiving deliveries. Traditionally, there is front desk staff to intercept any kind of office delivery. With staggered scheduling, remote and hybrid work, there is no guarantee that anyone will be in the office to receive those deliveries. This is causing a headache for offices who have to make trips directly to the carrier to pick up the package. Even worse, offices are having to deal with package theft.
Office managers are keen to be prepared in the event of a future pandemic
Since COVID-19, office security has also needed to take health into consideration. Temperature checks were required to access buildings, some incorporated contact tracing, and most buildings shut down completely. These are not sustainable practices, so office managers are now trying to create a plan to proactively prepare for the future through integrated capacity monitoring and health checking.
The Future of Physical Security in the Office
As the modern office evolves and faces new challenges, the workplace environment will adopt new trends as it pertains to physical security
Enabling Remote Management
The ability to remotely manage physical security is a necessity as companies begin to add more office spaces to their portfolio and as they implement remote work strategies. On-site credential management is no longer realistic in the modern work environment. Office managers or admins need to be on-site to navigate a complicated local system in order to make the simplest of updates, issue lost or stolen key cards, create visitor credentials, and more. This can also become a security concern if access needs to be revoked immediately, but there is no one who is able to make local changes in a timely manner.
Companies are quickly transitioning to cloud-based access control and security systems in order to manage the physical security of their offices from anywhere. Cloud-based security solutions operate from an off-site server (the cloud) and can be securely accessed by the appropriate admin so that no one has to be on-site to update employee or other user credentials. This allows companies to scale to additional satellite locations to accommodate remote work as well as ease the operational burden for managers while still maintaining and in many cases improving physical security.
Transitioning to Mobile Access Control
Traditionally, office access control systems issue key cards to employees in order to get into the building, office suite, elevators, shared amenities, etc. Managing this type of credential in an increasingly remote environment takes too much operational oversight. System administrators need to program cards on-site for new users and anytime a new card needs to be issued if an employee loses or forgets it. If an employee does lose their key card or it gets stolen or cloned, there is a physical security risk to the entire office which is a major liability.
Additionally, a key card at one office location will not necessarily work at another, regardless if the company is the same. Disparity in access control systems create a huge barrier for employees travelling to different offices frequently.
Finally, credential management with key cards becomes much more complicated when access doesn’t happen frequently. This is becoming more and more common with remote work policies and hybrid work. And the more complicated credential management becomes, the more gaps in physical security there are.
To better adapt to remote and hybrid work models and to accommodate streamlined access for more office locations, companies are adopting mobile access control. Mobile access control uses employee’s smartphones to unlock office doors. This provides a higher level of physical security for offices as an employee’s smartphone is directly tied to their own identity as opposed to a key card which is not linked to any one employee’s identity. This is how key cards become a security risk – they can be stolen and used to gain access to the facility because there is no way to verify if the person using the key card is the authorized employee.
Mobile credentials also offer a big leg up in security from traditional 125 kHz proximity cards, which can be cloned in many grocery store kiosks. Because credentials are stored on a phone, they inherently have 2-factor authentication since the phone needs to be unlocked for use. Further, in practice employees are much less likely to forget their phone versus a badge, which will help reduce the number of frantic calls to security that a badge was left at home.
Using mobile credentials for access control also allows companies to consolidate access. All office spaces use one consistent method of access – mobile phones. This allows travelling employees to streamline access regardless of the location they visit, which increases physical security because offices can maintain secure access points without worrying if an employee is stuck outside. Many offices, out of pure convenience, leave doors unlocked if they know they will have visiting employees.
Adopting Cloud-Based Security
Cloud-based security solutions, as mentioned above, are growing in popularity. Remote management is one of the primary reasons companies are adopting this operating practice, but there are other advantages to physical security as well.
Cloud-based systems allow admins to run access event reports for auditing purposes. Admins also have the ability to access and oversee all worksites under one platform, which gives them greater insight into office activity. This helps companies establish security patterns and makes it easier to identify anomalies in the future.
Using Identity for Physical Access Credentialing
An important change to office physical security, which is the theory behind mobile access control, is the transition to using identity as an authorizer for secure physical access. Simply, this means that authorized access is tied to the person’s identity as opposed to a parameter not tied to identity, such as a key card, which cannot be traced back to any one individual.
As mentioned above, companies are doing this to tighten their physical security strategy. Mobile access control is a popular, modern way to do this. Another physical access method using identity to authorize access is facial recognition access control.
Using biometrics like face recognition for employee access is an undeniable link to someone’s identity, which creates an airtight physical security strategy. To use face recognition, users self-enroll their biometric ID which is stored in a secure, encrypted system that will recognize the user’s face upon being shown to a facial recognition reader.
Integrated Video Intercom and Remote Unlock
Visitor management strategy is important for offices who need to grant access to clients, contractors, delivery personnel, maintenance, and cleaning staff – not just employees. Currently, visitor management practices in offices are broken in that it’s hard to tell at any given time who is in the facility. Sign-in sheets are hardly a good indication, plus they cannot be accessed in real-time. Visitor management software is effective only if it integrates with the access control system. Even then, visitor management software still does not have any physical access capabilities and only creates a partial solution.
Offices recognize that in order to have a complete physical security strategy, they need to integrate an intercom calling system for the office in order to seamlessly manage visitor access. Intercom systems allow office staff, typically the front desk or reception area, to receive a call from a visitor at a secure entrance, verify ID, and trigger a door unlock to grant access. But, traditional office intercom systems, like legacy access control systems, operate on-site, cannot be managed remotely, and have limited functionality.
Modern offices are upgrading their visitor management strategy by incorporating video intercom into their access control system. Video intercom allows the intercom call recipient to verify visitor ID visually and then remotely unlock the door for them. Modern video intercom allows intercom call recipients to receive video calls remotely via mobile or smart device. It doesn’t require anyone to be at an intercom receiving station that is wired throughout the building. Calls can be answered from anywhere and office doors can be unlocked after the visitor has determined the visitor can gain access. With delivery rates ever-increasing, and with offices more frequently empty, this feature proves invaluable in managing the secure delivery and tracking of on-site deliveries.
Visitors can be processed by security remotely through the same process, and issued a mobile credential, such as a PIN code, to gain access through pre-determined access control doors. Those same credentials can be set to expire automatically based on a time limit or number of uses, and can be contingent upon completing the health screening procedure. And with visitor management data stored in the cloud, the data can be used to help facilitate contact tracing if necessary. Altogether, this creates a completely secure and remote physical security strategy for offices.
Simplicity is Key
As firms have worked to tailor pandemic response strategies to their organization, facility management and human resources personnel have needed to take a more active role in the development of access control policies and procedures. However, many enterprise access control systems are complex to the point of needing weeks-long specialized training courses and are not accessible to non-technical users.
Further, turnover and staff cuts have resulted in employees taking on non-traditional roles and tasks. As a result, access control systems need to be simple, easy-to-learn, and intuitive for these users. Cloud-based systems that look and feel like modern interfaces that are familiar and simple will help these users become efficient at implementing and modifying procedures as necessary. These systems also need to have roles-based privileges in order to limit available options to a subset required to complete needed tasks only.
Start Improving Your Building Security
Get in touch with a Swiftlane specialist for more information on the best access control and video intercom solution for your building.