The data center industry is at the beating heart of the digital economy, and you can’t read the news today without hearing something about the huge investment in new data centers across the U.S. The Wall Street Journal reports that the four largest tech giants alone plan to invest nearly $400 billion in capital spending in 2025, mostly for AI-related data centers. From financial transactions to patient records and government systems, the world’s most sensitive data is processed and stored at these facilities. With so much at stake, access control for data centers is just as crucial as firewalls and encryption.
Access control for data centers ensures only authorized personnel can enter areas where sensitive data center hardware is maintained. This protects against downtime, breaches, and compliance failures. In this guide, we’ll explore the reasons for having robust access control in data centers, the common security challenges operators face, and the solutions that keep facilities secure and meet regulatory compliance. Whether you need to secure a small on-site data center for a mid-size company or are a contractor working on mega data centers for a tech giant, this guide covers the basics of access control in data centers.
Table of Contents
- What is Data Center Security
- Why Access Control For Data Centers Is Important?
- Common Challenges in Data Center Security
- Key Features of Modern Access Control Systems
- Compliance, Audit-Readiness, and Risk Mitigation
- Operational Reliability and Uptime Considerations
- A Brief Comparison of Leading Data Center Access Control Solutions
- Swiftlane – A Solution for Modern Data Centers
- Best Practices for Preventing Unauthorized Access
- Guidance for Selecting Access Control for Data Centers
- The Bottom Line on Data Center Physical Security
What is Data Center Security?
Physical security for data centers encompasses all the necessary tools to protect data center equipment. That includes protecting the physical racks of servers, electrical equipment, and cooling equipment from accidental or intentional damage or tampering by unauthorized individuals. While servers may have built-in digital software security to detect malware, hacking attempts, and other electronic means of disrupting the data center software, the physical security system must be designed to protect the hardware itself. Physical security works in conjunction with cybersecurity and network security to comprehensively protect data, system operations, and uptime. Effective defenses guard against both external intrusions and insider risks.
Why Access Control For Data Centers Is Important
Unlike office buildings or commercial spaces more generally, data centers – sometimes located within larger commercial spaces – are subject to high-stakes security requirements. A single breach can result in financial loss, unlimited liability, regulatory fines, and irreparable reputational damage. Downtime can mean significant loss of revenue and risk to the franchise as a whole.
- Protecting critical assets: Servers, networking equipment, and storage systems are prime targets for theft or sabotage. Not all risks involve hacking over networks; sometimes the risk comes in the form of physical infiltration of the systems.
- Mitigating insider threats: Employees and contractors may pose risks if access isn’t restricted and monitored. Only authorized and trained personnel should be able to access mission-critical data center hardware. All other parties should be accompanied and monitored at all times.
- Meeting regulatory compliance: Regulations that include SOC 2, ISO 27001, HIPAA, and PCI DSS, as well as GDPR in Europe, require strict physical security controls. This is particularly when data center hardware stores or processes confidential personal information in areas ranging from government services and healthcare to banking and financial transactions.
- Maintaining uptime: Unauthorized access or mishandling of infrastructure (by parties who aren’t properly trained on the equipment) can lead to costly service interruptions that can hit a business with lost revenues or losses due to a failure to meet service commitments.
- Business continuity: Securely storing business-critical information enables reliable access to all data needed for day-to-day operations and mitigates against franchise risk, revenue loss, or unexpected costs. Proper data center security can also help lower business insurance costs.
In short, access control isn’t just about keeping doors locked. Rather, it’s about protecting the integrity of the global digital economy.
Common Challenges in Data Center Security
Despite heavy investment, data centers face persistent challenges:
- Tailgating and piggybacking
Often, corporate and institutional data centers are located on-site within larger facilities. These house a mix of personnel types, including the general public. Unauthorized individuals in such mixed settings can sometimes gain access by following closely behind someone with valid credentials. - Layered access requirements
Security perimeters must account for different zones such as lobbies, data halls, cages, and even specific racks. An access control system for data centers must be able to differentiate between different classifications of employees and different zones. This is done based on the sensitivity of the equipment held in that zone. - Audit compliance
Many facilities struggle to produce accurate, audit-ready access logs that satisfy regulators and customers. Access control systems need to be able to track every person and the timeframes during which they had access to the data center hardware. - Contractor and visitor management
Short-term staff, such as outside IT contractors, need carefully controlled, time-bound access to prevent lingering permissions. Having a centralized visitor management system is key to addressing this issue. - Operational uptime
Access systems must remain functional 24/7, with redundancy to avoid lockouts or downtime.
These challenges create the need for advanced, integrated, and scalable access control systems. At the same time, many facilities don’t want to invest in a separate access control system just for an on-site data center. In this case, it is best to explore systems that can provide access control to an entire facility – such as a hospital, corporate office, or dedicated data center – while also offering different levels of access that keep data hardware separate from other general employee or guest access.
Key Features of Modern Access Control Systems
The latest generation of data center access systems go beyond keycards and PINs. Keycards and PINs can easily be stolen, cloned, copied, or used by an unauthorized individual. While that risk might be ok for a general office building, it’s too great when a data center carrying sensitive information is concerned. Here are the capabilities that matter most for meeting compliance standards and securing data:
Cloud-Based Access Control
This refers to systems that use centralized, remote control of credentials, permissions, and monitoring. By basing the system in the cloud, changes, like the addition or removal of personnel, can be applied across multiple sites. That way, a central security office or a third-party security contractor can manage and monitor all access points across multiple sites.
Biometric Access Control
Face recognition, fingerprint, or iris scans ensure that the person attempting to gain access really is the person who is registered to have permission. Biometrics align with zero-trust policies. That way, there can be no accidental leakage or sharing of PIN codes and no stealing of RFID tags. Only the authorized users programmed into the system can get in and their identities are verified in the moment with recorded and auditable logs.
Mobile Access Control
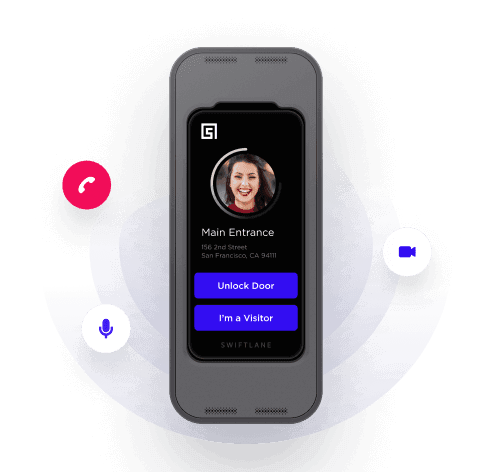
Secure, smartphone-based entry eliminates the risk of lost or cloned cards and uses the smartphone’s facial recognition to ensure that it is being used by the authorized user, not someone who stole it.
Audit-Ready Access Management
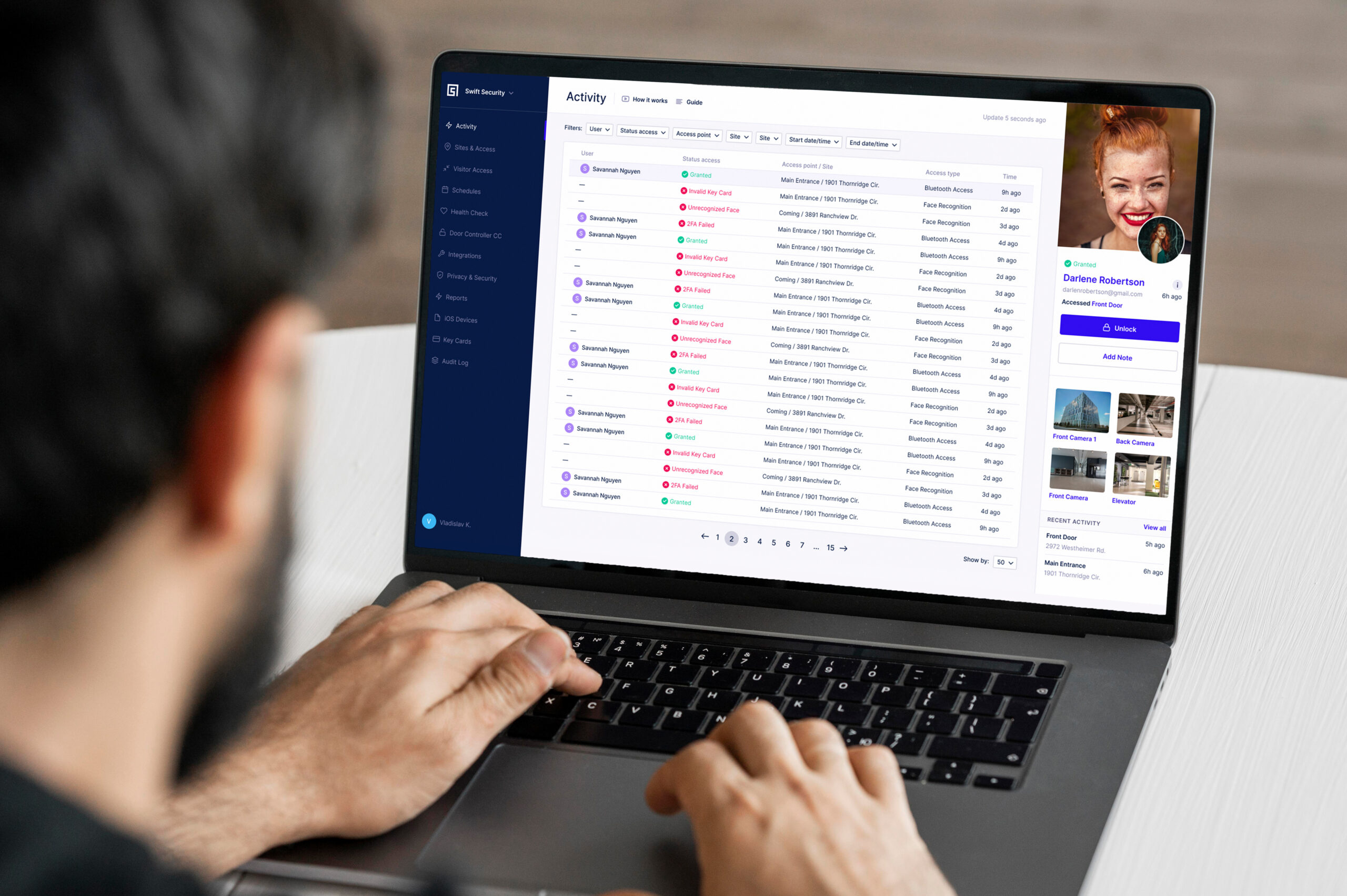
A system with automatic event logs tracks every access attempt, with exportable data for compliance reviews. With the most capable systems, these logs are stored in the cloud, allowing them to be accessed from anywhere, such as a central management office or by auditors, without requiring visits to each access control point or local facility hardware. This greatly helps save time and effort in maintaining logs to meet compliance standards.
Anti-Tailgating System
Mantraps, turnstiles, and AI-powered video analytics can detect and prevent unauthorized entry in conjunction with the access control system and guest management systems.
Integration With Surveillance
Access events link directly to video footage, creating a comprehensive incident record. This capability is enabled by access control systems integrations with facility closed-circuit camera systems, or by using access control intercoms with built-in cameras.
Compliance, Audit-Readiness, and Risk Mitigation
Regulators demand more than locked doors. They require documented evidence of security practices.
- SOC 2 Type II: This compliance standard demonstrates operational effectiveness of security controls, including physical access over an extended period of time via a thorough ongoing audit process. SOC2 compliance requirements demand access control systems that can filter personnel and create audit logs of who gained access.
- ISO 27001: This popular standard calls for controlled and monitored access to information processing facilities, including analysis of 14 categories of control tools and a continuous improvement plan.
- HIPAA & PCI DSS: These two industry-specific protocols, mandate restricted access to equipment handling sensitive healthcare (Health Information Portability and Accountability Act) or payment data (Payment Card Industry Data Security Standard).
Modern access systems reduce compliance burden with built-in reporting tools. Exportable access logs and audit trails provide proof of control and shorten audit cycles. This also supports risk mitigation, ensuring redundant systems prevent downtime and protect against lockouts.
Operational Reliability and Uptime Considerations
Beyond keeping data secure, the primary reason for data center access control is protecting sensitive equipment and maintaining server uptime. To achieve this, facilities benefit from:
- Fail-secure locks that default to locked if power fails, protecting assets without disrupting operations.
- Manual physical key overrides: Maintenance crew can access the facilities with physical backup keys in the event of an emergency or access control system failure.
- Redundant controllers and backup power supplies to keep systems running 24/7.
- Cloud failover to ensure access management remains available, even in regional outages.
- Predictive maintenance powered by analytics to anticipate hardware failures before they cause downtime.
A Brief Comparison of Leading Data Center Access Control Solutions
The data center security market is highly competitive. Here’s how major providers stack up:
| Provider | Strengths | Limitations |
| LenelS2 | Comprehensive, enterprise-grade features | Complex, less cloud-native |
| Avigilon | Strong in video surveillance and AI | Access control secondary to video |
| Gallagher | Perimeter and multi-layer security | High complexity systems that require specialized expertise |
| Swiftlane | Cloud-first, biometric, mobile-ready, and audit-friendly | Newer entrant with a growing data center footprint |
Swiftlane – A Solution for Modern Data Centers

While known primarily for residential and commercial security, Swiftlane is uniquely positioned to meet the demanding requirements of data centers:
- Cloud-native platform: You can manage credentials and reporting across multiple facilities from a secure cloud-based platform.
- Biometric and mobile access: Enhance security while improving convenience for staff and contractors. Our video intercom units use facial recognition with AI capabilities to identify each person trying to enter a facility and also identify tailgaters.
- Tailgating detection: Our AI-enhanced facial recognition system detects if there is another party lurking behind someone with access and alerts the authorized individual not to allow someone to tailgate into the door or gate.
- Unrecognized faces and audit trails: Unrecognized faces, such as of those trying to gain unauthorized entry, are captured and stored in the online database, which is useful for maintaining an audit trail and facilitating investigations of who may be trying to gain access.
- Compliance support: Our exportable logs and detailed reporting can simplify and expedite SOC 2, HIPAA, and PCI audits.
- Scale with your growth: Our system is designed to grow with facilities, whether adding racks, cages, or entire campuses. Our system can handle upwards of 10,000 unique users.
- Innovation focus: AI-powered analytics and a modern user interface (UI/UX) differentiate Swiftlane from many legacy incumbents.
- Highly durable hardware: Our video intercom access points feature IP65 weatherproofing and IK10 level anti-vandalism protection to keep facilities secure from potential attacks.
Best Practices for Preventing Unauthorized Access
Protecting a data center means going beyond the basics. Here are a few practical steps operators can take to tighten security and reduce risk:
- Use multi-factor authentication. A single card swipe isn’t enough; combining credentials such as an access card and a biometric check makes it far harder for someone to slip through.
- Stop tailgating. Physical barriers like mantraps, along with AI systems that spot people trying to follow closely behind someone else, help close one of the most common gaps.
- Layer your access policies. Not everyone needs to walk into every room. Restricting who can enter sensitive zones limits how much damage a stolen badge or misused credential can cause.
- Review access regularly. Old accounts and unused badges create vulnerabilities. A periodic review keeps the system clean and up to date.
- Control contractor and visitor access. Time-limited credentials and requiring escorts for guests prevent one-time visitors from becoming long-term risks.
- Tie access to video monitoring. Linking entry logs with surveillance footage makes it easier to verify that every access event was legitimate.
- Adopt a zero-trust mindset. Instead of assuming someone who’s in the building can be trusted everywhere, require verification at each door or checkpoint.
Guidance for Selecting Access Control for Data Centers
When evaluating access control systems, data center operators should consider:
- Compliance alignment: Does the system meet SOC 2, ISO 27001, HIPAA, or PCI DSS requirements? For European data centers, consider also the requirements of GDPR.
- Physical Durability: Access control hardware for mission-critical data centers should be resistant to extreme weather and physical attack, such as by carrying an IP65 and IK10 rating.
- Scalability: Can it expand seamlessly across multiple sites and facilities? Can it accommodate thousands of different users to scale with company growth?
- Integration: Does it connect with surveillance, alarms, and facility management platforms?
- Audit readiness: How quickly can it generate access logs for regulators or third-party auditors?
- User experience: Is it easy for staff and contractors to use? Can it be managed centrally without sending technicians to each access point in order to update the system?
By focusing on these criteria, organizations can select a solution that balances security, compliance, and operational reliability.
The Bottom Line on Data Center Physical Security
Data centers deal with a variety of physical security risks and demands, from preventing unauthorized access to maintaining regulatory compliance across different jurisdictions and industry norms. Today’s access control platforms serve multiple functions beyond basic security. They support audits, minimize operational risks, and help maintain critical uptime by preventing damage or tampering of the data center hardware.
Swiftlane can help you address these needs through cloud-based architecture, mobile and biometric access capabilities, and integrated audit reporting. Our centrally managed access control and visitor management features help operators enhance security without creating operational headaches.
As data centers grow more complex and face evolving threats, implementing comprehensive, compliance-focused access control becomes a top priority for protecting both infrastructure and the broader digital ecosystem.
If you want to learn more about how Swiftlane can help you protect your data centers, get in touch.